How to protect your smartphone against hackers
Although we can no longer do without our smartphones these days, we have to be extremely careful because they could be a lot more vulnerable than we might think. Hacking is no longer just an intriguing subject for Hollywood or even a threat to big corporations and multinationals alone.
Given the treasure trove of information we all carry around on our phones, be it locally or on the cloud, anyone could fall victim to a cyber criminal intent on stealing secrets or installing viruses on our phones that activate automatic clicks on adverts via our browsers (to increase investor profits), make the smartphone part of a botnet, or even turn it into an actual ATM. Some innovations have certainly made it harder to be deceived by these crooks (two-factor authentication for one) but there’s always a way to inflict damage, so it’s better to know your enemy and where they’re hiding if you want to avoid them.
Here are some tips to follow...
Here are some tips to follow...
. Keep away from public Wi-Fi

You may not have realized, but wireless hotspots in public places are an easy target for hackers. With the right skills and equipment, a criminal can see exactly what you’re doing online. This could include the e-mails you send, the login details you enter on social media, and even your financial data.
However, there’s an easy way to protect yourself against vulnerabilities when you’re near a public hotspot: just don’t use it. If you have to connect, the best way to do so is via a VPN like Avira Phantom VPN, express VPN which encrypts your activities. Private networks, which hide traffic packages, make it almost impossible to spy on you.
. Keep your device up to date
One of the simplest ways to protect your cell phone from unwanted attacks is to ensure that it’s up to date. Always keep your phone updated with the most recent operating system because updates are often specifically designed to close the loopholes that hackers have found a way to exploit, such as bugs, vulnerabilities, and zero-days.
For example, Google regularly releases security patches, as does Apple with its “minor updates” for iOS. More than just giving you the latest graphics or a few more emojis, the real value of these updates is in their potential to protect your device more effectively.
For example, Google regularly releases security patches, as does Apple with its “minor updates” for iOS. More than just giving you the latest graphics or a few more emojis, the real value of these updates is in their potential to protect your device more effectively.
. Ignore any spam
Junk e-mail is a favorite tactic among IT criminals. This includes suspicious links, password prompts and fake attachments that expose your phone to a particular threat when you click on them. The solution? Easy. Don’t follow up on spam from unknown senders and, if you recognize the first or last name, it’s better to take a closer look before pressing one too many buttons. Remember that no bank or credit institution will ask you to provide personally identifiable information via e-mail.
There are also a couple of quick strategies for telling if an e-mail is fake. Number one: Expand the sender’s address and try and see if it actually corresponds to the first name and last name shown. Number two: Hover your mouse over the link you’re being asked to click on to see if it really does direct you to the website of the organization that the message appears to come from (bank, agency, etc.).
. Use two-factor authentication

All major websites and apps now support two-factor authentication. This refers to the option of receiving a temporary code via a registered phone to be entered either when you access a profile from a new device, at random, at regular intervals, or as and when the system decides. So you may find yourself typing in more digits once you’ve accessed a social media account or other services, but this increases the level of protection because, if a third party tries to access another person’s account, they will be prompted to enter the very code sent by text message. Which only you have!
LEARN MORE...
LEARN MORE...
. Only install official apps
Another simple way for hackers to gain access to smartphones is to modify the code of certain well-known apps and hide their own malignant strings inside that contain viruses, malware and so on. There’s only one way to minimize this risk of infection, and that is to only download applications hosted by the original stores and avoid all other sources. We know the temptation is strong, especially in the Android world where single APKs are easy to install, even in manual mode (you just click on the folder where they are saved), and that is precisely why hackers try to inundate the web with fake WhatsApp Premium and Facebook Premium, exploiting what little information they find on someone.
. Never use unencrypted passwords
Assuming you no longer use strings such as “12345” or “0000” in your passwords, it is also a good idea to avoid saving text files in your phone’s memory that include passwords for the services you use.
So how do you remember them all? By using an app like Avira Password Manager, which uses a single master password to protect the others and is managed automatically by the applications on your phone.
. make the most of biometrics
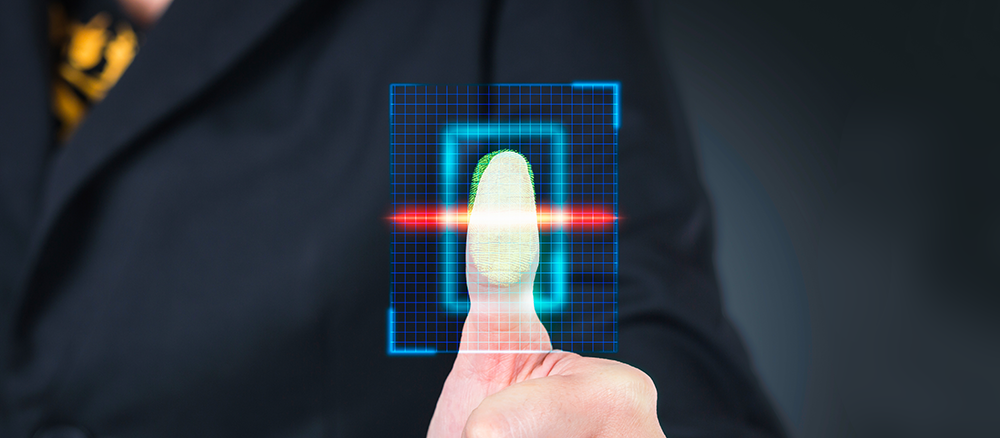
Biometric access significantly increases the level of protection on your smartphone. The concept is very simple: Instead of typing your username and password, all you need to do is put your finger on your phone’s sensor or let it scan your face (Face ID on iPhone X for example) to access your favorite software instantaneously. Previous generations of biometric scanners managed to bypass facial recognition simply by using photographs, but technological innovation has made chips more effective and more precise at looking for unique details that can only be identified from your face.
Erase your data when you sell your phone
Some people only buy mobile devices to look for clues left by their previous owners. If enough information is left on a phone, this could allow the new owner to carry out a sort of social engineering to discover usernames and passwords. What can they do with that information? Well, they can post compromising photos and videos, maybe fakes, and then demand a ransom to delete them, threatening to upload more.

Or they can exploit e-mail accounts to send messages containing malignant links from legitimate addresses in a tactic known as spear phishing. So make sure you carry out a hard reset before getting rid of your smartphone, by manually erasing multimedia content and accounts first of all and then perhaps downloading an app like Phone Check that tests the device’s internal cleanliness.













No comments:
Post a Comment